Your Guide to Commercial Intrusion Detection Systems
- Бонус за регистрацию онлайн казино
- Sep 10
- 16 min read
Think of a commercial intrusion detection system as your business's 24/7 watchtower. It’s a smart network of security tools designed to actively monitor your physical property or digital network for any sign of trouble. Instead of just reacting after a door has been broken down, it looks for suspicious behavior and alerts you the moment something is amiss.
The whole point is to get that crucial early warning, giving you a chance to act before real damage is done.
Understanding Your First Line of Defense

Let's stick with the watchtower idea. You’ve already got strong walls (firewalls), locked gates (access control), and maybe even guards at the door (passwords). An intrusion detection system, or IDS, acts as the sentinels patrolling those walls. They’re constantly scanning for anything that looks out of place.
An IDS isn't there to single-handedly stop an intruder. Its job is arguably more critical: to spot a potential threat the second it emerges and sound the alarm. This immediate alert gives your security team the jump start they need to investigate and shut down the threat before it can do any harm. Without that early warning, a breach could fly under the radar for hours, days, or even weeks—and by then, the fallout could be devastating.
Why Every Business Needs an IDS
In a world where security threats are getting smarter and more frequent, just having good locks on the doors isn't cutting it anymore. For small and medium-sized businesses especially, a solid commercial intrusion detection system is no longer a luxury. It’s a fundamental layer of defense that offers proactive protection, not just passive prevention.
An Intrusion Detection System observes, analyzes, and notifies. It hands your security team the intelligence they need to respond to threats that might otherwise go unnoticed until it’s far too late.
A modern IDS brings a few game-changing benefits to the table:
Proactive Threat Management: It helps you spot potential breaches before they escalate, protecting your assets, data, and your company's reputation.
Enhanced Security Awareness: The system gives you a real-time view of who is trying to get into your property or network, and when.
Support for Regulatory Compliance: Many industry rules, like HIPAA for healthcare or PCI DSS for payments, require you to have continuous monitoring in place to protect sensitive data. An IDS is built for exactly that.
Physical vs. Digital Sentinels
It’s easy to think of intrusion detection as a purely digital thing, but that’s only half the story. The same concept applies just as much to your physical office, warehouse, or storefront. An IDS can be a network of motion detectors and door sensors guarding your building, just as easily as it can be a sophisticated piece of software analyzing your network traffic.
Both types work on the same simple principle: they learn what "normal" looks like and then raise a red flag when something deviates from that baseline. Whether it's a strange login attempt from an unknown device at 3 a.m. or a motion sensor tripping in a secure area after hours, the system detects the anomaly and alerts the right people. This dual approach—protecting both your physical and digital worlds—is the bedrock of any truly comprehensive security plan.
How a Modern IDS Actually Works
To really get a feel for what a modern commercial intrusion detection system can do, it helps to look under the hood. It’s not some single, magical black box. Instead, think of it as a highly coordinated security team for your property, where each member has a specific and vital job.

This team has three core players: the Sensors, the Analysis Engine, and the Alerting Console. They work together in a seamless flow—observe, analyze, and act—to keep a constant watch over your business. Let's break down what each one brings to the table.
The Sensors: The Eyes and Ears on the Ground
First up are the sensors. These are the frontline data collectors, the eyes and ears of your entire system. We place them strategically throughout your building or property to watch everything that’s happening. Their only job is to tirelessly gather raw information that will be used to spot anything out of the ordinary.
Just like a security guard can't watch every door at once, a single sensor can only see so much. That's why a good IDS uses a variety of them to create a tight web of coverage.
Physical Sensors: These are the ones you can see and touch. Think motion detectors in hallways, magnetic contacts on doors and windows, or even vibration sensors on walls. For high-security sites, this could include thermal cameras or buried fiber-optic cables along a fence line.
Digital Sensors: In the world of cybersecurity, these sensors are code-based. They monitor your network for suspicious data packets or keep an eye on critical server files for unauthorized changes.
Each sensor simply reports what it detects. It doesn't decide if something is a threat—it just passes the raw data up the chain for the next component to sort out. This division of labor is what makes the system so efficient.
The Analysis Engine: The Brain of the Operation
Once a sensor picks something up, that data flows straight to the Analysis Engine. This is the central processor, the true brain of the whole commercial intrusion detection system. Its job is to take the constant flood of information from all the sensors and make sense of it, filtering out the noise to find the signals that point to a real threat.
Imagine a security expert watching dozens of CCTV monitors at once. They aren't just staring at screens; they're comparing what they see against their years of experience to tell normal activity from suspicious behavior. The Analysis Engine does the exact same thing, just at a massive scale and in microseconds.
The engine uses smart algorithms to analyze patterns. It cross-references incoming data against a huge library of known threats or a baseline of what’s considered "normal" for your specific business.
For example, if a door sensor is triggered at 3:00 AM on a weekend, the engine knows this is outside of normal business hours. If network sensors see repeated failed login attempts from an unknown location, the engine flags it as a possible cyberattack. It’s all about connecting the dots to turn raw data into security intelligence you can actually use.
The Alerting Console: The Communication Hub
The final piece of the puzzle is the Alerting Console. When the Analysis Engine identifies a credible threat, it doesn't just sit on that information. It immediately sends an alert to the console, which is designed to get the right information to your security team, right now.
This isn't just a loud, generic alarm. A modern console gives your team rich, detailed context so they can respond effectively. A typical alert might include:
The exact location: "Motion detected in Warehouse Section B."
The time and date of the event.
The specific threat type: "Forced entry attempt on rear door."
Supporting evidence, like a video clip from a nearby camera.
This instant, detailed notification is what makes an IDS so powerful. It closes the loop between simply monitoring and actively defending, giving your team the head start they need to investigate and stop a threat before things get out of hand.
Comparing the Different Types of Intrusion Detection Systems
Picking the right commercial intrusion detection system isn't about finding a single "best" solution. It’s about finding the right fit for your business, your assets, and your unique operational flow. Think of it as tailoring a security plan—the first step is understanding the fundamental tools at your disposal.
Intrusion detection systems are generally broken down in two ways: first, by where they look for trouble, and second, by how they spot it. Each approach has its own strengths and is designed for different security goals.
Where the System Looks for Threats
The first big question is about vantage point. Is your system watching all the traffic flowing in and out of your digital property, like a guard at the main gate? Or is it stationed inside a critical room, watching over your most valuable assets? This is the core difference between Network-based and Host-based systems.
A Network-based Intrusion Detection System (NIDS) is that guard at the main gate. It's strategically placed on your network to inspect all the traffic moving between your devices and the outside world. This wide-angle view is perfect for catching broad threats like network scans, malware spreading across multiple machines, or denial-of-service attacks.
On the other hand, a Host-based Intrusion Detection System (HIDS) is the specialist guard inside a specific high-value room. It lives on an individual device—like your main file server, a point-of-sale terminal, or a key executive’s laptop. A HIDS monitors the internal activities of that one machine, looking for red flags a NIDS would never see, such as unauthorized changes to critical files or suspicious software being installed.
How the System Identifies Threats
The second piece of the puzzle is how the system decides if something is a threat. This comes down to the detection method. Imagine the difference between a bouncer checking IDs against a list of known troublemakers versus an experienced floor manager who can spot trouble just by sensing a change in the room's atmosphere.
Signature-based detection is the bouncer with the list. It relies on a constantly updated database of "signatures"—unique digital fingerprints of known viruses, malware, and attack patterns. If it sees traffic that matches a signature on its list, it immediately blocks it or sends an alert. It’s incredibly fast and accurate for stopping common, well-documented attacks. The catch? It can't stop what it doesn't know. A brand-new, "zero-day" attack will walk right past it.
Anomaly-based detection works like that experienced floor manager. Instead of looking for known threats, it spends time learning what "normal" looks like for your specific network. It establishes a baseline of your typical data flows, who logs in when, and what files are usually accessed.
Anomaly-based systems are all about spotting deviations. When something happens that's way outside that established baseline—like a massive file transfer to an unknown server at 3 AM from a user who always works 9-to-5—the system flags it as suspicious.
This approach is brilliant for catching new and sophisticated attacks that signature-based systems would miss. Its main challenge is the potential for false alarms if your "normal" suddenly changes for a legitimate reason and the system hasn't caught up yet.
The image below gives a great visual comparison of how professionally managed commercial systems stack up against common open-source alternatives.
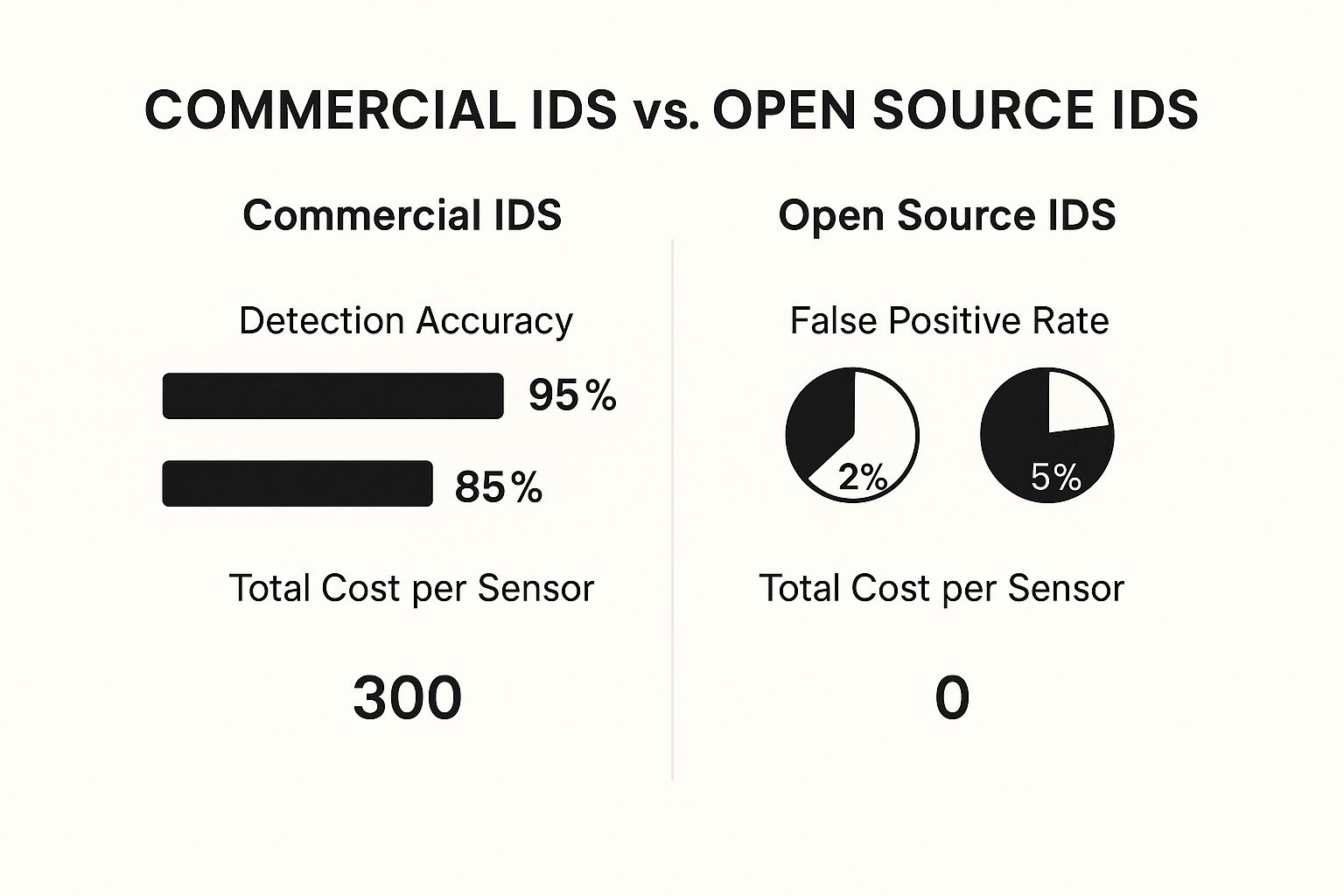
As you can see, while open-source tools seem attractive with no upfront cost, commercial solutions deliver far greater accuracy and fewer false positives. That translates directly into less wasted time for your IT or security team investigating non-threats.
Making the Right Choice for Your Business
To help you decide what combination makes the most sense, this table breaks down the key differences.
Comparison of IDS Types and Detection Methods
System Type / Method | How It Works | Best For | Key Advantage | Potential Drawback |
|---|---|---|---|---|
Network-based (NIDS) | Monitors traffic across the entire network from a central point. | Detecting external threats, network scans, and widespread malware. | Broad visibility of all network activity. | Can't see encrypted traffic or activity happening on an individual device. |
Host-based (HIDS) | Runs on a specific device (server, workstation) and monitors its internal activity. | Protecting critical servers, spotting unauthorized file changes, and insider threats. | Deep visibility into a specific machine's health and integrity. | Can be complex to manage across hundreds or thousands of devices. |
Signature-based | Compares activity against a database of known threat signatures. | Stopping known, common viruses, malware, and well-documented attacks. | Very high accuracy with low false positives for known threats. | Completely blind to new "zero-day" attacks without a known signature. |
Anomaly-based | Establishes a baseline of "normal" behavior and flags significant deviations. | Detecting novel, sophisticated, and zero-day attacks; insider threats. | Ability to identify brand-new threats that have never been seen before. | Can generate false positives if "normal" activity changes unexpectedly. |
Ultimately, there’s no single right answer. The strongest security postures almost always use a hybrid approach, layering different commercial intrusion detection systems to create a defense-in-depth strategy.
You might use a NIDS to guard your network perimeter while deploying HIDS on your most sensitive database servers. At the same time, you can combine a signature-based engine to catch all the low-hanging fruit with an anomaly-based system to watch for anything new or unusual. This layered model gives you the most comprehensive protection against the widest range of threats.
Why Your Business Needs an Intrusion Detection System Right Now

In today's business world, it's no longer a question of if you'll face a security threat, but when. The dangers have moved far beyond a simple break-in or a basic computer virus. We're now up against attackers who are patient, skilled, and often well-funded, making a proactive defense non-negotiable.
This is exactly where a commercial intrusion detection system (IDS) goes from being a "nice-to-have" gadget to a core part of your business's survival strategy. Think of it as your ever-watchful security guard, spotting sophisticated threats designed to slip past standard defenses like firewalls and locked doors. Without it, you’re essentially flying blind.
The Game Has Changed: A New Wave of Threats
Today’s attackers don’t just kick down the front door. They use quiet, multi-stage attacks designed for maximum impact. A crippling ransomware attack can bring your entire operation to a standstill in minutes. Even worse, advanced persistent threats (APTs) can hide in your network for months, silently stealing sensitive data.
And don't make the mistake of thinking this is only a problem for big corporations. Attackers often view small and medium-sized businesses as easy targets precisely because they assume security resources are limited. This makes solid SMB cybersecurity absolutely critical. For an SMB, a single breach can be devastating, leading to massive financial losses and a reputation that’s hard, if not impossible, to repair.
An IDS is your digital and physical early-warning system. It’s not just about stopping a burglar; it's about spotting the subtle signs of a coordinated attack before it fully unfolds, protecting your assets and your customers' trust.
This escalating danger is why we're seeing huge investments in security. The market for commercial Intrusion Detection Systems is expected to jump from USD 6.8 billion in 2025 to a staggering USD 22.2 billion by 2035. This growth is driven by one simple fact: businesses need better tools to fight back.
It's Not Just Security—It's a Business Imperative
Beyond preventing attacks, an IDS is crucial for keeping your business running and meeting a growing list of regulatory demands. Many industries now have strict rules that require constant monitoring to protect sensitive data.
PCI DSS: If you process credit cards, the Payment Card Industry Data Security Standard requires you to have systems that detect and respond to security incidents.
HIPAA: For healthcare organizations, the Health Insurance Portability and Accountability Act demands diligent monitoring to prevent unauthorized access to patient records.
GDPR: The General Data Protection Regulation has strict rules for protecting the data of EU citizens, and the penalties for slipping up are severe.
Falling short of these standards isn't just about risking a data breach. It can lead to crippling fines, legal battles, and a complete loss of customer trust.
A good IDS gives you the audit trails and real-time alerts you need to prove you're doing your due diligence and staying compliant. It turns security from a simple expense into a business advantage, showing your clients and partners that you take protecting their information seriously. In that light, investing in a robust commercial intrusion detection system isn't just a security decision; it's a direct investment in your company's future.
How AI Is Making Intrusion Detection Smarter and Faster
If you think of a traditional security system, you might picture a simple tripwire. It’s effective, sure, but it can't think, learn, or adapt. All it knows is "if this, then that." Artificial intelligence (AI) is completely rewriting that script, upgrading commercial intrusion detection systems from basic alarms into smart defense platforms that can spot threats with uncanny accuracy.
Think of it like having an old-school security guard who's walked the same halls for 20 years. He knows the building's rhythm—the normal sounds, the familiar faces, the exact time the cleaning crew shows up. He doesn't just react to a loud bang; he notices the subtle stuff, like a door that's usually locked being left ajar or a strange car sitting in the parking lot for hours. AI-powered systems do the same thing, just on a scale no human team could ever hope to match.
Moving Beyond Simple Rules
The real game-changer with AI is its ability to move from a rigid, rule-based approach to a more fluid, adaptive one. Instead of just checking against a list of known threats, AI and machine learning algorithms first learn what "normal" looks like for your specific business. It builds a unique operational fingerprint for your property or your network.
Once it has that baseline, the system becomes incredibly good at anomaly detection. It's constantly watching and flagging anything that deviates from the established norm. This could be anything from:
An employee trying to access a secure server room at 3:00 AM when they’ve only ever worked a 9-to-5 shift.
A slow, steady trickle of network traffic heading to an unrecognized external server, a classic sign of someone trying to sneak data out.
A few minor, unrelated sensor pings across the building that, when pieced together, reveal the pattern of a coordinated break-in.
This knack for spotting the unusual is what makes AI systems so powerful against brand-new, zero-day attacks that would sail right past traditional defenses.
Cutting Through the Noise of False Positives
Anyone who's managed an older intrusion detection system knows the pain of "alert fatigue." When a system constantly cries wolf—flagging a gust of wind as a person or routine maintenance as a cyberattack—your team starts to tune it out. That's how real threats get missed.
AI solves this by adding a crucial layer of context. It learns the difference between a raccoon scuttling past a motion sensor and a person deliberately jimmying a lock. This intelligence filters out the noise, so your team only gets high-fidelity alerts they need to act on.
This shift toward smarter systems is driving massive industry growth. The global market for intrusion detection and prevention systems was valued at USD 6.31 billion in 2024 and is expected to skyrocket to USD 20.18 billion by 2034. That incredible jump is all about the growing need for defenses that can keep up with increasingly sophisticated threats. You can dig into more about these market dynamics to see where the industry is heading.
On top of that, AI helps automate the first steps of incident response. Instead of just dumping a raw alert on your team, the system can serve up correlated data and actionable insights in seconds. This speed and precision make your entire security operation more effective, turning your IDS from a passive alarm into an active partner in your defense.
Choosing the Right Commercial IDS for Your Business
Alright, let's turn all this theory into action. Picking the right commercial intrusion detection system isn't about chasing the latest tech—it's about finding the right fit for your actual, day-to-day business operations. This is where you map out a clear, practical plan to make sure you're investing in a solution that genuinely protects your assets and gives you a solid return.
Making a smart choice starts with being honest about your specific vulnerabilities and goals. The system that works wonders for a small retail shop will be completely wrong for a sprawling warehouse or a multi-story office building.
Start by Evaluating Your Core Needs
Before you even think about looking at different vendors or product spec sheets, you need a crystal-clear picture of what you're actually trying to protect. This goes way beyond just the four walls of your building. We're talking about your people, your equipment, and your data.
Taking the time for this initial assessment will help you zero in on the features that matter and steer you away from paying for bells and whistles you’ll never use.
Ask yourself these three critical questions:
What are we really worried about? Is it a classic after-hours break-in? Is internal theft a bigger concern? Or do you have a specific high-stakes area, like a server room or a safe, that needs Fort Knox-level security?
How does our business operate? Are you a 24/7 facility, or is the property a ghost town after 5 PM? Knowing when you're most vulnerable is half the battle.
Do we have any compliance hoops to jump through? If you’re in an industry governed by regulations like PCI DSS (for credit cards) or HIPAA (for healthcare), you’ll need specific monitoring and reporting capabilities baked into your system.
Answering these questions first creates a profile of your ideal system. It makes the whole process of shopping around much easier because you can immediately weed out the solutions that just don't fit.
Key Factors for Comparing Systems
Once you have your requirements checklist in hand, you can start sizing up the different commercial intrusion detection systems out there. It’s tempting to just look at the price tag, but you have to think about the total value and how the system will hold up over time. Three things are non-negotiable: scalability, integration, and the quality of support you'll get.
1. Scalability for Future GrowthYour business isn't static, and your security system shouldn't be either. A system that can't grow with you—whether you're adding a new wing to your building or opening another location—is a dead-end investment. You need to ask vendors, "How painful is it to add more sensors, cover more doors, or even bring a whole new building online with your system?"
2. Seamless System IntegrationAn IDS that works all by itself is missing the point. The real power comes when your intrusion detection system talks to your other security tools, like your access control keycards and your video surveillance cameras. This is how you create a truly unified security front. For example, when a back door sensor is tripped, it should automatically tell the nearest camera to start recording and pop that video feed up on your screen. That’s immediate, actionable intelligence.
3. Quality of Vendor SupportAn intrusion detection system is not something you just set up and walk away from. You're entering a long-term relationship with the vendor. Look for a company with a solid reputation that provides real support, from helping with the initial setup to training your staff and being there when you need technical help down the road. Good support is what keeps your system effective, updated, and reliable.
To put this in perspective, you have to consider the world we're operating in. Sophisticated threats are on the rise, and that’s a huge driver for better intrusion detection. In 2023, things like banking trojans and botnets were involved in about 31% of cyberattacks globally. This pressure is exactly why businesses are taking a harder look at their security. You can find detailed insights on how cyber threats drive IDS adoption on gminsights.com to see the bigger picture.
Got Questions About Intrusion Detection? We've Got Answers.
Diving into the world of commercial intrusion detection systems can feel a bit overwhelming at first. Let's tackle some of the most common questions business owners and site managers ask when they're getting started.
What's the Real Cost of a Commercial IDS?
There's no one-size-fits-all price tag. For a small office needing just a few sensors, you might be looking at a few hundred dollars. But for a large warehouse that needs a sophisticated, multi-layered system, the investment could easily run into the tens of thousands.
The final cost really boils down to a few key things:
The number and type of sensors: How many motion detectors, door contacts, or vibration sensors do you need?
The "brains" of the system: Are you going with a basic analysis engine or one powered by advanced AI?
Where it lives: Will you have on-site hardware or go with a more flexible cloud-based solution?
Service and support: Don't forget to factor in professional installation and any ongoing monitoring fees.
Can an IDS Actually Stop a Break-In on Its Own?
In a word, no. An IDS is your digital lookout—its job is to spot trouble and sound the alarm immediately. It's a detection tool, not a physical barrier.
Think of it this way: the IDS is what gives you the critical early warning needed for a human (or another system) to respond effectively. It works best when paired with an Intrusion Prevention System (IPS), which can take action by locking doors or automatically alerting the authorities.
An IDS gives your security team intelligence. An IPS gives them automated enforcement. The strongest defense always uses both, creating a layered security strategy that works.
How Is an IDS Different From My Video Cameras?
This is a great question, as they often work hand-in-hand but have very different jobs. Your video surveillance system is the historian; it records everything visually, which is invaluable for evidence after something happens.
An IDS, on the other hand, is the real-time analyst. It actively sifts through data from its sensors to detect a potential breach as it’s happening and trigger an instant alert. The magic happens when you integrate them: an IDS sensor trip can tell the nearest camera to start recording and push that live feed directly to your security team, letting them see exactly what's going on.
Ready to secure your property with a system that detects threats before they escalate? PCI Audio-Video Security Solutions designs and installs advanced intrusion detection, access control, and surveillance systems built around your specific business needs. Protect your assets with confidence by visiting us at https://www.pciavss.com to schedule a consultation.







Comments