Explore Types of Intrusion Detection Systems That Protect Your Network
- Бонус за регистрацию онлайн казино
- Jun 26
- 14 min read
When you start digging into types of intrusion detection systems (IDS), it helps to think of them as different kinds of security guards. Some are posted at the main gate watching all the traffic coming and going, while others are assigned to guard a specific, high-value room. Similarly, some guards have a book of known troublemakers to watch out for, while others are trained to spot any behavior that just seems off.
Getting a handle on these two core distinctions—where an IDS watches and how it watches—is the first step to building a truly effective security posture.
What Is an Intrusion Detection System?

Simply put, an Intrusion Detection System is a monitoring tool that acts as a silent alarm for your digital environment. Its primary job isn't to stop an attack in its tracks, but to spot suspicious activity as it happens and alert the right people. Think of it less like a brick wall and more like the advanced, intelligent surveillance systems from a company like PCI AVSS, which constantly watch for anything out of the ordinary.
While a firewall is a gatekeeper that decides what traffic gets in or out, an IDS works quietly in the background, observing everything that’s already inside. It’s looking for patterns of malicious behavior, signs that security policies are being violated, or anything that deviates from established norms. This early warning is what gives your security team a fighting chance to investigate and neutralize a threat before real damage is done.
The Two Foundational Categories of an IDS
Every IDS can be sorted into two main groups, and understanding both is crucial. It’s a bit like describing a car; you wouldn't just say it's "a sedan," you'd probably also mention if it's "a hybrid sedan." One part describes its form, the other its function.
For any IDS, these two defining traits are:
Deployment Location: This simply answers, "Where does the system live?" The answer is either on the network itself or on a specific device (a host).
Detection Method: This answers the question, "How does it spot trouble?" It either looks for known, pre-defined attack signatures or it learns what "normal" looks like and flags anything that doesn't fit that baseline.
Key Takeaway: An IDS is all about visibility. It’s the eyes and ears of your security operation, giving you the critical intelligence needed to understand what's actually happening on your network and respond with purpose.
This dual-classification system is what makes the different types of intrusion detection systems so versatile. You can mix and match them to create layers of defense. For instance, you could use a network-based system to monitor your entire network's perimeter while deploying a more sensitive host-based system on a critical server that stores all your customer data.
Network-Based Intrusion Detection Systems (NIDS)
Picture a security guard standing at the single main entrance to a massive, bustling office building. Instead of checking IDs at every single office door, this guard monitors everyone who comes in and out of the main lobby, watching the flow of traffic for anything suspicious. This is exactly how a Network-Based Intrusion Detection System (NIDS) works.
A NIDS doesn't live on any individual computer. It’s strategically placed at a key point in your network, like a junction on a busy highway—often just inside the main firewall. From there, it watches all the data packets moving back and forth across the entire network, giving it a bird's-eye view of all activity.
How a NIDS Protects Your Entire Network
By monitoring the whole network, a NIDS casts a very wide net. It isn't concerned with the inner workings of a single machine; it's focused on the communication between all the machines. This broad perspective makes it exceptionally good at spotting large-scale attacks.
Here are a few common threats a NIDS is built to catch:
Unauthorized Port Scanning: Think of this as a burglar rattling all the doorknobs on a street. A NIDS sees this systematic probing for open, vulnerable entry points.
Denial-of-Service (DoS) Attacks: This is when an attacker floods your network with junk traffic, creating a digital traffic jam that prevents legitimate users from getting through.
Malware Spreading: If a virus or worm gets onto one machine, its first move is often to try and spread to others. A NIDS can spot that lateral movement.
This ability to see everything from one spot is a huge plus. It’s often much easier and more cost-effective than installing and managing separate security tools on every single device. It's such a popular approach that network-based systems command the largest slice of the global IDS market, making up approximately 55% of the market share. For more on this, you can check out the IDS market report from SkyQuestt.com.
Key Strengths and Limitations
Of course, no security tool is perfect. The biggest advantage of a NIDS is its incredible visibility. By watching all the traffic, it makes it really hard for an attacker to move around the network without tripping an alarm. A single NIDS device can protect hundreds of hosts without you ever needing to install software on them.
Crucial Insight: The real power of a NIDS is its wide-angle lens. It excels at catching threats that impact the network as a whole, acting as a critical guard at your perimeter and other important internal choke points.
However, this broad view has one major blind spot: encryption. As more and more web traffic becomes encrypted (using HTTPS), the NIDS can see that data is moving, but it can't read what's inside the packets. It's like seeing a sealed, opaque envelope—you know it's there, but you have no idea what the letter inside says. A threat hidden in that encrypted data can slip right past.
Furthermore, on extremely busy networks, a NIDS can sometimes struggle to keep up. If the volume of traffic is too high, it might become a bottleneck and slow things down, or even worse, start dropping packets and miss a potential threat.
Host-Based Intrusion Detection Systems (HIDS)

While a network-based system acts like a security camera watching the main entrance, a Host-Based Intrusion Detection System (HIDS) is more like a personal security detail assigned to a specific VIP. Instead of watching the flow of traffic across the entire network, a HIDS is software installed directly onto an individual machine—the "host."
This could be a critical file server holding your company's crown jewels, a point-of-sale terminal processing customer payments, or an executive's laptop. This up-close-and-personal approach gives it a completely different, and incredibly detailed, point of view.
A Look Under the Hood
A HIDS doesn't really care about the raw network packets flying around. It's interested in what happens after those packets arrive and the operating system unwraps them. Think of it as an internal auditor for the machine it lives on. It takes a baseline snapshot of the system's normal state and then relentlessly compares it to the live system, looking for any deviation that spells trouble.
This granular focus allows a HIDS to spot threats that would be completely invisible to a network-level system.
So, what is it actually looking for?
System Log Clues: It sifts through system, application, and security logs, searching for suspicious patterns like a barrage of failed login attempts or unusual error messages.
File Integrity: It keeps a hawk-eye on critical system files. If a core file (think on a Windows server) is suddenly modified, deleted, or swapped out, the HIDS sounds the alarm. This is a classic malware move.
Suspicious Processes: The HIDS monitors all running processes to see if a malicious program has been launched or if a legitimate application starts acting erratically.
Configuration Drift: It will flag unauthorized changes to user accounts or security settings, like a standard user suddenly trying to grant themselves administrator rights.
This hyper-focused monitoring provides a powerful, final layer of defense. Even if an attacker slips past your firewalls and network defenses, the HIDS sitting on the target machine can be the last thing standing between them and a successful breach.
Key Advantage: A HIDS has a superpower: it can see inside encrypted traffic. Because it runs on the host itself, it analyzes data after it's been decrypted. This neatly sidesteps the major blind spot that often stumps network-based systems.
The Downside of a Detailed View
Of course, this incredible level of detail comes with some trade-offs. The main challenge is deployment and management. Since you have to install the HIDS software on every single device you want to protect, it can become a real headache in a large organization. Imagine rolling out updates and managing alerts from thousands of individual endpoints—it requires a solid central management console and dedicated staff.
There's also a performance cost. The HIDS agent uses some of the host's CPU and memory, which could potentially slow down the very machine it's trying to protect.
But for your most critical assets, that trade-off is almost always worth it. A HIDS gives you a precise, last line of defense right where it matters most.
Signature vs. Anomaly: How an IDS Actually Detects Threats
Once you've decided where to post your digital security guards—on the network or on individual hosts—the next big question is how they’ll spot trouble. This choice gets to the very heart of how an IDS works, defining its entire strategy.
Ultimately, it comes down to two core methods that power nearly all types of intrusion detection systems. Think of it as choosing between a detective who works off a list of known criminals versus a behavioral analyst who knows a system so well they can sense when something is just slightly off.
Signature-Based Detection: The "Wanted Poster" Approach
The most common and straightforward method is signature-based detection. I like to explain this with a simple analogy: imagine a security guard at a checkpoint, armed with a thick binder full of "wanted" posters. Each poster has a detailed description of a known bad actor—a specific piece of malware, a virus, or a documented attack pattern.
As data flows past the IDS, it’s constantly checked against this library of known threat signatures. If a piece of data matches one of the "posters," the system immediately sounds the alarm. It's an incredibly reliable and fast way to catch the usual suspects.
Key strengths of this method include:
High Accuracy: It's looking for exact matches, which means very few false alarms. When a signature-based IDS flags something, you can be pretty confident it's the real deal.
Simplicity: The logic is easy to grasp and implement. The system's effectiveness really just hinges on having an up-to-date signature database.
Low Resource Use: The matching process isn't computationally demanding, so it rarely slows down your network or systems.
But this method has one glaring, critical weakness: it can't see what it doesn't already know. A brand-new threat that doesn't have a "wanted poster" yet—what we call a zero-day attack—will walk right by a purely signature-based system completely undetected.
Anomaly-Based Detection: The Behavioral Analyst
This is where anomaly-based detection provides a much-needed different perspective. Instead of looking for known threats, this approach spends its time learning what "normal" looks like for your environment. Once it establishes that baseline, it flags anything that deviates from it.
Picture a seasoned security guard who has patrolled the same building for a decade. They know every employee's routine, which doors are used at what times, and even the normal hum of the building's machinery. If an unfamiliar face tries to access a secure floor at 3 AM using a stolen keycard, the guard will immediately recognize the situation as an anomaly, even if the person isn't on a criminal watchlist.
That's exactly how an anomaly-based IDS operates. It uses machine learning to build a sophisticated profile of normal network traffic, CPU usage, user activity, and data access patterns over time.
Crucial Insight: Anomaly-based detection is your number one defense against new, sophisticated, or zero-day threats. It doesn’t need a pre-existing "wanted poster" to know that a user suddenly trying to exfiltrate gigabytes of data to an unrecognized server is highly suspicious.
The infographic below highlights some key performance metrics you'll want to consider when weighing different IDS options.
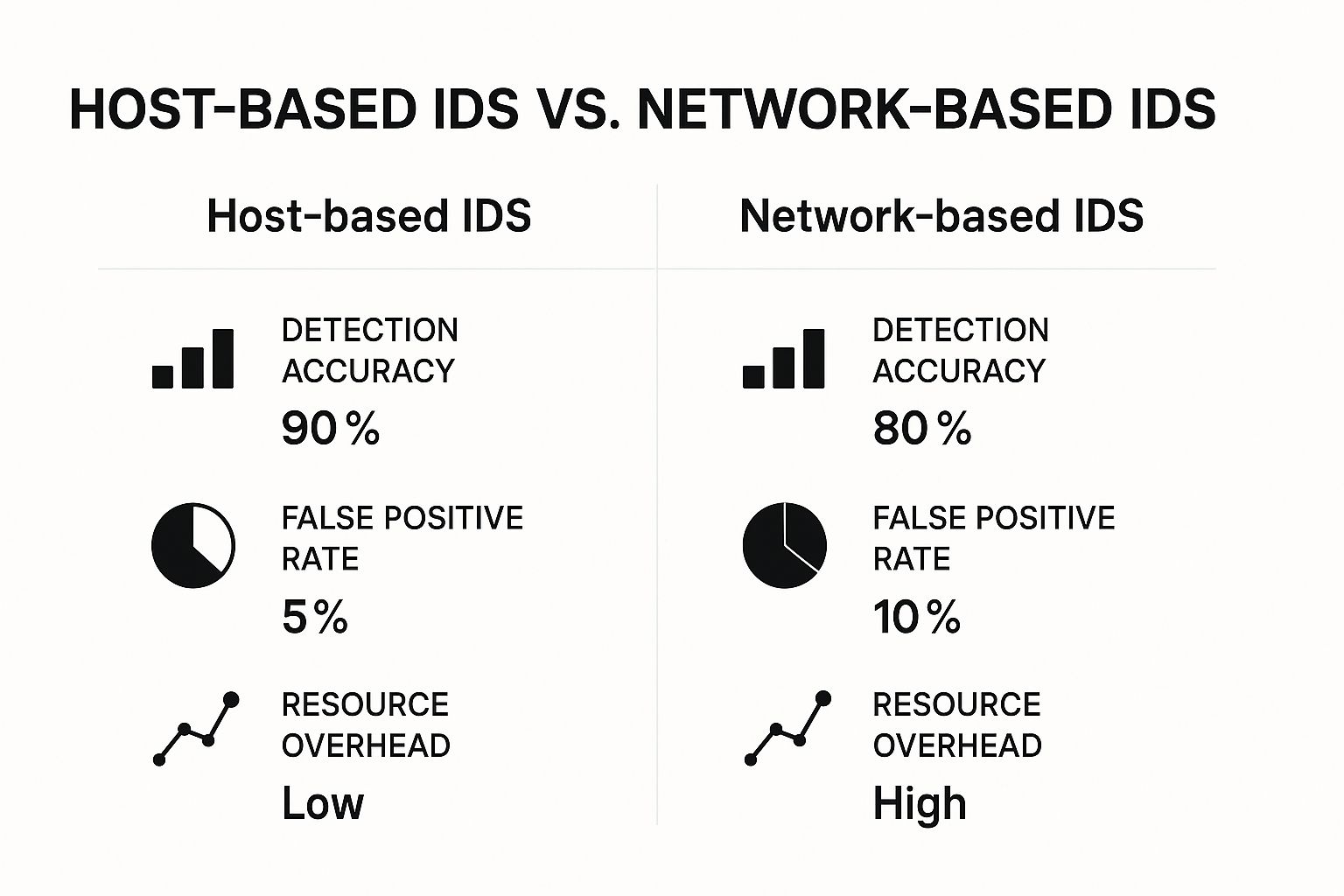
The data here shows that while a Host-based IDS (HIDS) might offer higher detection accuracy, it often comes at the cost of greater resource usage compared to a Network-based IDS (NIDS). Market analysis confirms that anomaly-based detection has become essential for finding new threats, which is why it's now widely used alongside signature-based methods. If you'd like to dive deeper, you can discover more insights about intrusion detection market trends.
The primary trade-off with anomaly detection is the higher potential for false positives. Sometimes, a legitimate but unusual activity—like an admin running a rare diagnostic tool—can trigger an alert, requiring a bit more investigation.
Comparison of Detection Methods
Choosing between these two isn't always an either-or decision. Most modern security setups use both. The table below breaks down their core differences to help you understand where each one shines.
Feature | Signature-Based Detection | Anomaly-Based Detection |
|---|---|---|
Primary Goal | Identify known threats by matching signatures. | Identify unknown threats by spotting deviations from normal behavior. |
Detection Speed | Very fast for known threats. | Slower, as it requires analysis and comparison against a baseline. |
Key Strength | Extremely high accuracy with very few false positives. | The ability to detect novel, zero-day attacks. |
Main Weakness | Completely blind to threats without a known signature. | Can generate more false positives from legitimate but unusual activity. |
Resource Needs | Low. Requires minimal processing power. | High. Needs significant processing and memory to maintain the baseline. |
Maintenance | Requires constant updates to the signature database. | Requires an initial "learning period" and periodic retraining. |
Ultimately, a signature-based system is your reliable guard against the well-known criminals, while an anomaly-based system is the smart detective looking for any behavior that just doesn't add up. For a truly robust security posture, you need both.
So far, we’ve looked at intrusion detection systems as separate tools—you either watch the network or you watch the individual machines. But modern attacks aren't that simple.
Attackers rarely stick to one path. They might poke around your network, find a weak spot, and then pivot to attack a specific server. They blend known exploits with brand-new techniques. Since threats come from multiple angles, your defenses need to as well. Relying on just one type of IDS leaves you with blind spots, and those are exactly what attackers hunt for. This harsh reality has pushed the security industry toward smarter, blended defense models.
From Silos to Synergy: The Hybrid IDS
This is where the Hybrid Intrusion Detection System comes in. Don't think of it as a brand-new invention; it’s more of a "best of both worlds" strategy. A hybrid IDS combines network-based (NIDS) and host-based (HIDS) monitoring into one unified system. The goal? To give you a complete, panoramic view of your security posture.
Imagine you have security cameras watching all the doors and hallways of your building (that's your NIDS). You also have motion detectors and alarms inside your most critical rooms, like the server room or the vault (that's your HIDS). A hybrid system is the central security desk that sees the alerts from both sources at the same time.
The NIDS might spot broad threats like a port scan sweeping across your network, while the HIDS on a key database server simultaneously alerts you to a suspicious process trying to access sensitive files. By connecting these two dots, the system can identify a complex, multi-stage attack that each tool might have missed on its own.
The Big Idea: A hybrid IDS gets rid of the "either/or" dilemma. It layers network and host visibility to build a true defense-in-depth strategy, closing security gaps and giving your team much clearer, more actionable alerts.
Specialized Systems for Specific Jobs
Beyond the hybrid model, the security world has also developed highly specialized systems for niche tasks. The most common one you'll run into is the Protocol-Based Intrusion Detection System (PIDS).
A PIDS is a specialist. It focuses entirely on a single communication protocol, most often HTTPS, to protect web servers. Think of it as a translator who is not only fluent but is also an expert in the subtle nuances and dialects of a single language. It can spot tiny, malicious manipulations in web traffic that a general-purpose NIDS might not be trained to see.
This layered approach is quickly becoming the new standard. In fact, hybrid systems that mix signature, anomaly, and behavior-based techniques now account for an estimated 20-30% of all IDS deployments. This trend shows a clear industry shift away from single-point solutions. You can dig deeper into IDS market adaptations in this research report.
Ultimately, the goal is to combine these different perspectives to gain the comprehensive visibility you need to stand a fighting chance against today's sophisticated attackers.
Choosing the Right IDS for Your Environment
Picking from the different types of intrusion detection systems isn't just a technical purchase; it's a strategic move. The "best" IDS has nothing to do with having the most features or the highest price tag. It's about finding the one that fits your organization's real-world operations and security goals like a glove. To get it right, you need to take an honest look at your specific situation.
Start by asking a few fundamental questions. How big and complicated is your network? What's your budget, not just for the initial setup but for the long-term care and feeding of the system? And who is going to run it—do you have a seasoned security team ready for a complex tool, or do you need something that's more hands-off?
The answers to these questions will point you toward a solution that actually makes your life easier, not harder.
Matching Your IDS to Your Assets
The smartest security strategies almost always involve a layered approach. Think of it as placing the right kind of guard in the right place. For a small business, a Network-Based IDS (NIDS) can be a fantastic starting point, watching over the network's perimeter like a hawk. It provides a wide, affordable net to catch common threats trying to get in from the outside.
But what if that same business has a single server holding all of its sensitive customer data? A NIDS can't see what's happening on that server. That’s where a Host-Based IDS (HIDS) becomes essential. By installing it directly on that critical machine, you get a dedicated guard watching for any suspicious internal activity—something a network-level tool would be completely blind to.
Strategic Insight: A strong defense isn't about picking one IDS type and calling it a day. It’s about layering them to create overlapping fields of vision. This ensures your most critical assets get the focused attention they deserve.
For any organization that has to meet strict compliance rules, like PCI DSS for handling payment card information, this kind of layered security isn't just a good idea—it's a requirement.
Key Factors for Your Decision
Before you sign on the dotted line, run through this checklist. Making sure these factors align will save you a world of headaches down the road.
Network Environment: Where does your infrastructure live? Is it all on-premise, fully in the cloud, or a hybrid mix? This will be a major factor in deciding between a physical appliance and a virtual or cloud-native solution.
Compliance Needs: Are you bound by regulations like HIPAA or PCI DSS? These standards often come with very specific rules about logging, monitoring, and file integrity—tasks that a HIDS is built to handle.
Integration: How will the new IDS play with your existing security stack? Consider your firewall and even physical security tools, like surveillance systems from providers such as PCI Audio-Video Security Solutions. You need a system that integrates smoothly and gives you clear, actionable alerts, not just more noise.
Answering Your Top IDS Questions
Even after you've got a handle on the different types of intrusion detection systems, some practical questions always seem to pop up. Let's dig into a few common ones to clear up how these systems actually behave in the real world.
What's the Real Difference Between an IDS and an IPS?
The biggest difference boils down to one word: action.
Think of an Intrusion Detection System (IDS) as your silent watchdog. It sits quietly, observing everything that happens on your network or on a specific computer. If it spots something fishy, it barks—sending an alert to let you know. It’s a passive monitor, providing crucial intel but never jumping into the fight itself.
An Intrusion Prevention System (IPS), on the other hand, is more like an active security guard. It doesn't just watch; it acts. Positioned directly in the flow of traffic, an IPS spots a malicious attempt and immediately blocks it, stopping the attack dead in its tracks. It's an active, in-line defense.
Can an IDS See Threats Hidden in Encrypted Traffic?
This is a huge challenge, and the answer depends on the type of IDS. For a Network-Based IDS (NIDS), encrypted traffic is essentially a locked box. It can see the box go by, maybe even guess what's inside based on its size and shape (metadata analysis), but it can't open it to see the actual contents. This creates a massive blind spot.
A Host-Based IDS (HIDS) has a clever workaround. It sits on the end device itself—the very place where data gets decrypted. By inspecting traffic right after it's been unwrapped and before an application uses it, a HIDS can spot threats that were completely hidden from the network's view.
Which IDS is the Right Fit for a Small Business?
For most small businesses, a cloud-based NIDS or a modern firewall with integrated IDS capabilities is a fantastic, budget-friendly starting point. It gives you a great bird's-eye view of your network security without breaking the bank.
But don't stop there. If your business has a high-value asset—say, an e-commerce server handling customer payments—it's incredibly wise to add a HIDS to that specific machine. This layered strategy gives you the best of both worlds: broad network monitoring combined with laser-focused protection where it counts the most.
Protecting your business means building a complete security picture, covering both your digital and physical spaces. PCI Audio-Video Security Solutions specializes in advanced camera and access control systems that create a truly secure environment. Secure your premises with our expert solutions.







Comments