A Guide to Industrial Security Solutions
- Бонус за регистрацию онлайн казино
- Jul 6
- 18 min read
When we talk about "industrial security," we're no longer just talking about a chain-link fence and a night watchman. The game has changed. Today, it’s a sophisticated blend of physical and digital defenses designed to protect your entire operation—your people, your expensive assets, and the very processes that keep your business running.
What Do We Mean by Modern Industrial Security?

Think of your industrial site like a modern-day fortress. The old way of thinking—tall fences and a few guards—was the equivalent of stone walls. It worked for its time. But the threats we face now are far more complex, slipping through cracks you didn't even know existed.
That’s where modern industrial security solutions come in. This isn't about buying a few cameras and a new lock. It's about building an interconnected ecosystem where every security component talks to the others. It's a strategy of defense-in-depth, with each layer backing up the next to create a truly tough barrier against theft, sabotage, or intrusion.
To really grasp this, let's break down the core components that make up a robust security plan. Think of them as the pillars holding up your entire defensive strategy. When they work together, the whole is far greater than the sum of its parts.
The Core Components of Industrial Security
Security Pillar | Primary Function | Fortress Analogy |
|---|---|---|
Surveillance | Provides visual oversight and intelligent monitoring | Your all-seeing watchtowers |
Access Control | Manages and logs all entry and movement | Your gates and trusted gatekeepers |
Alarms & Detection | Delivers immediate alerts to active threats | Your ever-vigilant sentinels |
An alarm that triggers a camera to zoom in on a breach while automatically locking down nearby doors? That's the kind of smart, unified response that stops an incident in its tracks—something standalone systems could never do.
When Physical and Digital Security Collide
Here’s the biggest shift I've seen in my career: the line between a physical break-in and a digital one has completely blurred. Your Operational Technology (OT)—the complex web of hardware and software running your machinery and processes—is now a massive target.
A hacker gaining control of your OT can cause more damage than a dozen people with crowbars. They can shut down production, destroy equipment, or create catastrophic safety failures from half a world away.
Protecting your digital infrastructure is just as important as guarding your physical perimeter. A modern security strategy must treat them as two sides of the same coin, creating a unified defense against all potential threats.
This isn't just a hypothetical, either. The money follows the risk. The industrial cybersecurity market is projected to jump from USD 24.04 billion in 2024 to USD 25.71 billion in 2025.
That rapid growth is being driven by the very real threats that facility managers are facing every day. You can dig deeper into the trends shaping the industrial cybersecurity market to see why this is happening. A holistic view that combines tough physical security with smart cybersecurity isn't just a good idea anymore. It's absolutely essential for staying in business.
The Three Pillars of Physical Industrial Security

When you're tasked with securing an industrial facility, it helps to think like you're defending a fortress. But instead of moats and drawbridges, a modern site is protected by a trio of technologies working together. These three pillars—surveillance, access control, and intrusion detection—are the bedrock of any serious physical security plan.
Sure, each one provides a basic level of protection on its own. But their true strength is revealed when you unify them into a single, cohesive system. This integration lets them share information and automate responses, creating a smart, proactive defense that’s much tougher to beat.
It's no surprise that the global demand for these integrated systems is climbing. The overall security solutions market is projected to reach about USD 379.3 billion in 2025, a noticeable jump from USD 354.7 billion in 2024. This growth is directly tied to the urgent need to protect critical infrastructure, where this combination of video, access, and alarms is fast becoming the standard. You can dig into the latest market growth projections to see just how big this trend is.
Pillar 1: Industrial Surveillance as Your All-Seeing Eyes
The first pillar is industrial surveillance—your eyes and ears on the ground. This is a world away from the cameras you see at a local shop. Industrial environments are harsh, unforgiving places, often filled with dust, extreme temperatures, vibrations, and even potentially explosive atmospheres. Your surveillance gear has to be tough enough to handle it all.
This means deploying specialized cameras as essential tools in your security arsenal. For instance:
Thermal Cameras: These cameras see heat, not light, making them perfect for spotting an intruder in total darkness or through smoke and fog. They can even identify overheating machinery long before it fails.
Explosion-Proof Cameras: In places like chemical plants or refineries, a single spark could be catastrophic. These cameras are built into rugged, sealed enclosures that prevent them from igniting flammable gases or dust in the air.
4K and High-Resolution Cameras: For a massive site like a logistics hub or manufacturing plant, you need the ability to zoom in on tiny details from far away. This is crucial for identifying people, reading license plates, or getting a clear picture of an incident.
But modern surveillance isn't just about passively recording video. It’s about intelligent analysis. Built-in artificial intelligence (AI) and machine learning analytics turn your cameras into active guards, automatically flagging unusual activity—like someone lingering in a restricted area or a vehicle going the wrong way—and instantly alerting your team.
Pillar 2: Access Control as Your Digital Gatekeeper
Next, you need to lock down your doors and gates. Access control systems are the digital gatekeepers that decide who can go where, and when. In an industrial setting, the old lock-and-key system just doesn’t cut it anymore; there’s no audit trail, and a single lost or stolen key can compromise your entire site.
Modern industrial security solutions offer much more precise control, using credentials that are tough to copy and can be revoked instantly.
An effective access control system doesn’t just keep the wrong people out; it creates a detailed, real-time log of all movement within your facility. This audit trail is indispensable for incident investigation and compliance.
Imagine a sprawling manufacturing plant with sensitive R&D labs, hazardous material storage, and high-value inventory zones. A unified access control system makes sure only authorized staff can get into these specific areas. This is usually done with a mix of technologies:
Biometric Readers: Using fingerprints, facial recognition, or iris scans, biometrics offer top-tier security because the "key" can't be lost, stolen, or handed off to someone else.
Mobile Credentials: Employees can use their smartphones as secure access keys. This makes life easier for everyone and allows you to grant or revoke access instantly from a central dashboard.
Keycards and Fobs: While more traditional, modern encrypted cards are still a very reliable and affordable choice for many situations, especially when layered with other security measures.
Pillar 3: Intrusion and Alarm Systems as Your Sentinels
The final pillar is your network of sentinels—the systems that sound the alarm at the first hint of trouble. Intrusion and alarm systems are designed to detect unauthorized entry or emergencies and trigger an immediate, decisive response.
These systems create a protective bubble around and inside your facility using a wide array of sensors, each with a specific job. For a large perimeter, you might use fence-mounted vibration sensors or infrared beams that create an invisible tripwire.
Inside, motion detectors, glass-break sensors, and door contacts watch for any unauthorized access. The real magic happens when these systems are integrated with the other two pillars. For example, when a perimeter sensor is tripped, the system can instantly tell nearby cameras to zoom in on the breach, turn on floodlights, and send a live video feed straight to the security team's phones. This layered, integrated strategy is the hallmark of a powerful industrial security solution.
Why Cybersecurity Is Your Digital Drawbridge

Think of your facility's physical security like the thick stone walls of a medieval castle. They’re impressive, but completely useless if an attacker can just lower the drawbridge and waltz right in. In today's industrial world, your computer network is that digital drawbridge.
For decades, we had it easy. The systems controlling physical processes—what we call Operational Technology (OT)—were completely separate from the corporate IT network. They were "air-gapped," living in their own isolated world, safe from the digital threats outside.
That era is long gone. Now, we're connecting everything. Industrial control systems (ICS) and SCADA systems are being plugged into corporate networks to pull data, boost efficiency, and allow for remote management. This has undeniable benefits, but it also smashes those old walls to pieces, creating a huge, inviting doorway for cyberattacks. A breach that once might have only risked customer data can now trigger a physical catastrophe on your factory floor.
This is exactly why any modern industrial security solution has to be aggressive on the digital front. Your security cameras and access gates are just one piece of the puzzle. Without strong cybersecurity, they can be bypassed or, even worse, turned against you by an attacker who seizes control of your network.
Understanding Your New Attack Surface
When we connect OT systems to the internet, we're throwing them into the same shark-infested waters that IT networks have been swimming in for years. But the stakes are wildly different. In an OT environment, we're not just worried about someone stealing data; we're worried about safety and availability. A disruption here can have immediate, real-world consequences, affecting human lives and the continuous operation of critical infrastructure.
Look at the infamous 2021 Colonial Pipeline attack. The hackers got in through a single compromised password for an old, forgotten VPN account. They didn't even touch the pipeline itself. Instead, their ransomware encrypted the IT systems needed to bill customers, forcing the company to shut down a massive portion of the East Coast's fuel supply. It’s a perfect, painful example of how an IT breach can bring physical operations to a grinding halt.
These attacks highlight a difficult truth: our OT systems are often riddled with known vulnerabilities. Much of this equipment is old, designed long before anyone was thinking about cybersecurity. You often can't patch or update it without risking a costly production shutdown.
Fortifying Your Digital Defenses
Protecting this newly converged IT/OT environment demands a different security mindset and a specific set of tools. You can't just slap standard IT security software onto an OT network; it's too aggressive and can disrupt sensitive, finely-tuned processes. The focus has to shift from blocking threats to containing and controlling them.
Two core strategies are the bedrock of modern OT security:
Network Segmentation: This is all about dividing your network into smaller, isolated zones. Think of it as building fire doors and internal walls inside your castle. If an attacker breaches a low-risk area—like the guest Wi-Fi—segmentation stops them from moving laterally into a critical zone, like the network controlling your assembly line. It contains the damage.
Zero-Trust Architecture: The old model of "trust, but verify" is dead. A zero-trust approach works on a much simpler principle: "never trust, always verify." It assumes threats are already inside your network, not just outside. Every single user, device, and application has to be authenticated and prove it has permission to access any resource, every single time. No one gets a free pass.
A siloed approach to security is no longer viable. With digitization, OT, IT, and cloud domains are deeply interconnected. Unified visibility across all domains is essential to detect advanced threats and orchestrate an effective response.
Putting these strategies into practice isn't just a technical project; it's a fundamental culture shift. It forces your IT and OT teams, who have often worked in completely separate worlds with different priorities, to finally start collaborating.
The True Cost of a Digital Breach
A successful cyberattack on your operational systems can be absolutely devastating. You have the immediate financial hit from production downtime, sure. But the consequences quickly cascade into regulatory fines, irreparable damage to your reputation, and even environmental or safety disasters.
The attempted hack on the water treatment facility in Oldsmar, Florida, is a chilling reminder of how quickly a digital intrusion can become a public safety crisis. Investing in robust cybersecurity as a core part of your industrial security solutions isn't just a good idea—it's non-negotiable. It's the only way to secure that "digital drawbridge" and ensure your physical fortress is truly impenetrable.
Choosing Your Security Deployment Model
Once you've mapped out the physical and digital defenses you need, the next big question is where your security system will "live." This isn't just about physical placement; it's about how the system’s data and management software are hosted and accessed. This decision, known as the deployment model, has a ripple effect on everything from your initial budget and long-term costs to how your team manages security day-to-day.
Think of it like deciding on a command center for a military base. Do you want a self-contained bunker with every control right there on-site? Or would a more flexible command post, accessible from anywhere in the world, be better? Maybe you need a bit of both. Each option has its own set of pros and cons, tailored to different operational needs and financial realities.
The three main choices for modern industrial security solutions are on-premise, cloud-based, and hybrid. Let's dig into what each one really means for your facility.
On-Premise Solutions: The Traditional Fortress
An on-premise setup is the classic, time-tested approach. In this model, all your security hardware—servers, data storage, and management software—is physically located at your facility. Your team is completely responsible for buying, installing, and maintaining every piece of the puzzle.
It’s like owning your own private power plant. You have total control and it keeps running even if the public grid fails, but you're also on the hook for all the fuel, upkeep, and repairs. This is a big responsibility.
This model is often the top choice for companies with stringent data privacy regulations or those in remote areas where internet service can be spotty at best. The biggest advantage is having absolute control over your system and data, since nothing ever leaves your site. The trade-off? A much larger upfront investment and the ongoing headache and cost of managing the IT infrastructure yourself.
Cloud-Based Solutions: The Flexible Command Post
On the flip side, you have cloud-based systems. With this model, often called Security as a Service (SaaS), all the heavy lifting is handled for you by a provider like PCI Audio-Video Security Solutions. Your cameras and access control readers simply connect over the internet to powerful servers in a secure, off-site data center.
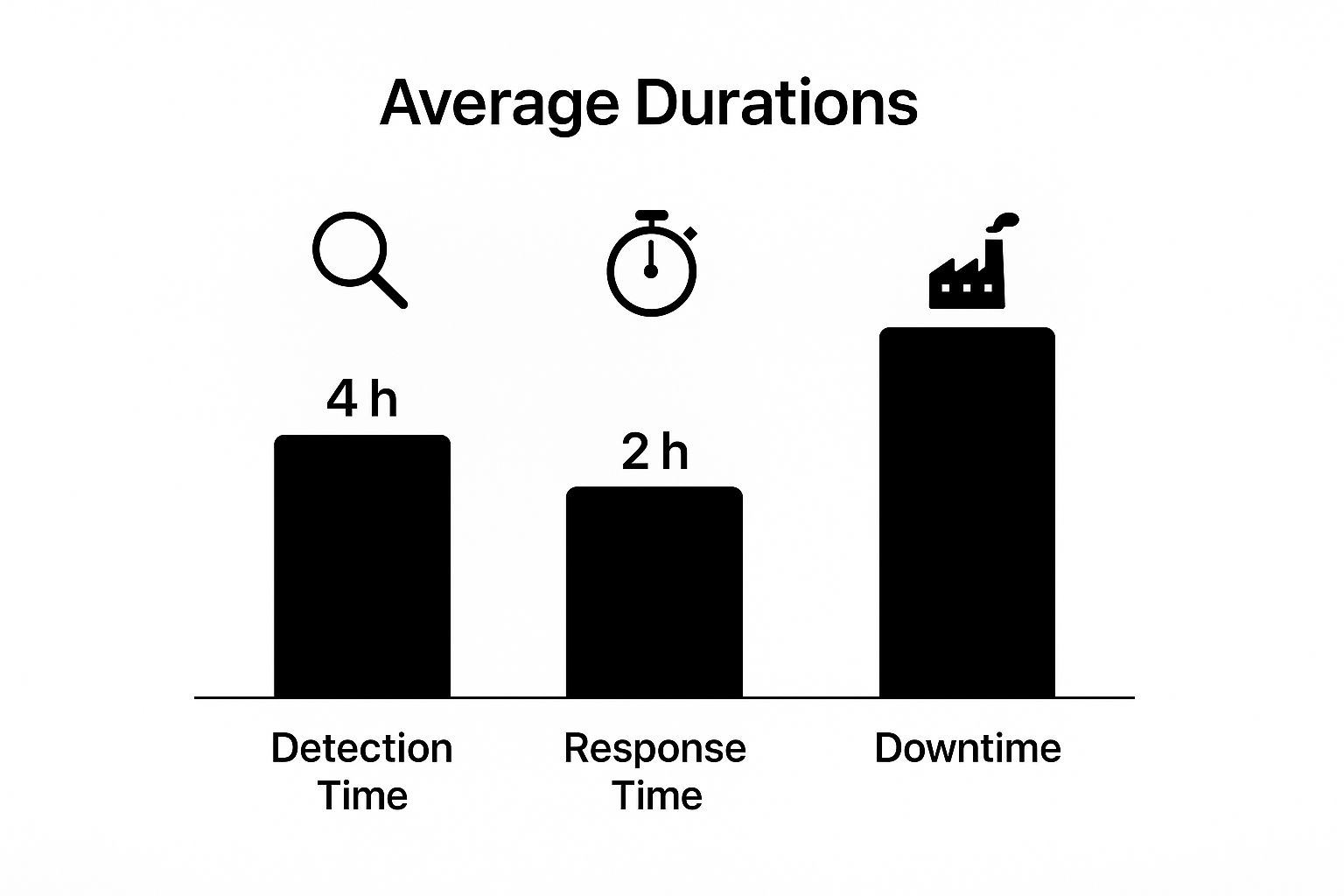
The image above shows just how critical these systems are—201 days to detect and 70 days to contain a breach are industry averages. A well-deployed system can slash these numbers, directly reducing costly downtime.
You manage everything through a simple web browser or a mobile app. The provider takes care of all the software updates, security patches, and server maintenance. This approach drastically lowers your initial costs, turning a huge capital expense into a predictable monthly or annual operating expense. The major wins here are massive scalability, the freedom to manage your system from anywhere, and taking a huge load off your internal IT staff.
Hybrid Solutions: The Best of Both Worlds
A hybrid model doesn’t force you to choose. Instead, it strategically blends on-premise and cloud elements to give you a potent mix of reliability and flexibility. It’s built on the idea that not all security functions have the same requirements.
A hybrid approach is often the sweet spot for industrial facilities. It lets you keep mission-critical functions local for rock-solid reliability while tapping into the cloud for its convenience and advanced features.
For instance, you might record high-definition video from your most important cameras to a local server. This ensures you never miss a thing, even if your internet connection drops. At the same time, you could use a cloud platform to manage employee access credentials, check live video feeds remotely, and get instant alerts on your phone. This gives you the resilience of on-premise recording with the modern, flexible management of the cloud. It's no wonder this is fast becoming the preferred setup for complex industrial environments.
Choosing the right model is a critical decision that balances control, cost, and convenience. To make it clearer, here’s a breakdown of how the three models stack up against key business factors.
Comparing Security System Deployment Models
Factor | On-Premise | Cloud-Based (SaaS) | Hybrid |
|---|---|---|---|
Upfront Cost | High (servers, software licenses, installation) | Low (minimal hardware, subscription-based) | Moderate (some on-site hardware plus subscription) |
Ongoing Costs | Moderate to High (maintenance, IT staff, upgrades) | Predictable (fixed subscription fees) | Mixed (subscription plus some on-site maintenance) |
Scalability | Difficult (requires purchasing new hardware) | Easy (adjust subscription plan as needed) | Flexible (scale cloud services easily, on-prem as needed) |
Data Control | Complete (data never leaves your site) | Vendor-Managed (data stored in the cloud) | Balanced (critical data on-site, other data in cloud) |
Remote Access | Limited/Complex (often requires a VPN) | Excellent (access from any browser or app) | Excellent (cloud components are fully remote) |
IT Burden | High (your team manages everything) | Very Low (vendor handles maintenance, updates) | Low to Moderate (vendor manages cloud, you manage local) |
Ultimately, the best model depends entirely on your facility's specific security protocols, budget, and operational needs. By understanding these trade-offs, you can select a deployment strategy that provides robust protection today and can adapt to your needs tomorrow.
Calculating the ROI of Your Security Investment
If you’re still looking at security as just another line-item expense, it's time for a serious mindset shift. Thinking of it as a "cost" is not just outdated; it's dangerous. A well-designed security strategy isn't a drain on your resources—it's a high-value investment that protects your entire operation from catastrophic failure.
The real question isn't, "How much does this cost?" It's, "What's the staggering cost of doing nothing?" When you start thinking in those terms, the business case for a comprehensive security system becomes crystal clear. A single major incident, whether it's a break-in or a sophisticated cyberattack, can easily cause financial damage that dwarfs the cost of the system that would have stopped it in its tracks.
The Tangible Returns on Security
I get it—calculating the ROI for security can feel a bit like trying to measure something that didn't happen. But there are absolutely tangible, quantifiable benefits that show up directly on your bottom line.
The most obvious one is reducing direct losses. This is everything from preventing the theft of expensive raw materials and finished products to stopping thieves from ripping out copper wiring or making off with heavy machinery. Every asset you protect is money that stays in your business.
Then there's the massive cost of operational downtime. Think about it: an act of sabotage or a major breach could shut down your production lines for hours, if not days. Every single minute your facility is offline means lost revenue, missed deadlines, and potentially even contractual penalties.
Downtime Prevention: A security system that prevents just one major shutdown can pay for itself almost instantly.
Reduced Vandalism: Proactive surveillance and solid access control are powerful deterrents to vandalism, saving you a fortune in repair costs over time.
Lower Insurance Premiums: This is a big one. Many insurance providers offer hefty discounts to facilities that have a professionally installed and monitored security system. That's a direct, recurring saving, year after year.
The Intangible Gains That Drive Real Value
Just as crucial are the intangible benefits. These are a bit harder to stick a price tag on, but they're absolutely essential for long-term success and creating a resilient, efficient business.
First and foremost is employee safety. When your team feels safe and secure—free from the threat of intrusion or workplace violence—you see morale and productivity go up, while turnover goes down. People who feel protected can focus on doing their best work.
Investing in security is fundamentally an investment in operational continuity and trust. It reassures your employees, customers, and partners that your facility is a stable, reliable, and well-managed operation.
That sense of stability bleeds directly into your brand reputation. In our hyper-connected world, a major security failure can quickly spiral into a public relations nightmare, wiping out customer trust and damaging your market standing. On the flip side, a strong security record builds confidence and can become a real competitive advantage.
Keeping Pace with the Growing Threats
The urgency for these solutions is only increasing as the threat landscape expands. The market for industrial cybersecurity solutions and services, valued at USD 20.52 billion in 2024, is expected to jump to USD 23.9 billion in 2025. Why? Because cyberattacks are happening at a frightening rate—over 2,400 times a day worldwide. You can dig into more of this data by checking out the industrial cybersecurity market report.
When you add it all up—the hard savings from preventing theft and downtime, plus the invaluable benefits of a safer workplace and stronger brand trust—the ROI on security becomes undeniable. Putting money into high-quality industrial security solutions isn't just a defensive move. It's a smart, proactive business strategy that protects your assets, your people, and your future profitability.
So You’ve Installed a New System. Now What?
Getting your new security system up and running is a major step, but it’s just the beginning. The real work starts now. To truly protect your investment—and your facility—you need a solid plan for managing it over the long haul. Without one, even the most sophisticated industrial security solutions will eventually fail, leaving you with glaring blind spots and a false sense of security.
Think of it like buying a brand-new truck for your fleet. You wouldn't just drive it off the lot and forget about oil changes or tire rotations, right? It’s the same with your security system. Ongoing, proactive management is what keeps it running smoothly, protecting your people and assets day in and day out. You have to shift from a reactive, "fix-it-when-it-breaks" mentality to a continuous cycle of improvement.
Start with a Real-World Risk Assessment
Before you can manage anything, you have to know exactly what you’re up against. A thorough risk assessment is your strategic roadmap, and it needs to go far beyond generic checklists. This is about identifying the specific, unique vulnerabilities of your facility.
Get your boots on the ground. Walk the entire property, from the perimeter fence right down to the most critical zones on your production floor, and start asking the hard questions. Where are our most valuable assets stored? Which areas are the easiest targets for a break-in? What’s the worst-case scenario if someone gets into this specific area? This kind of detailed, hands-on analysis is the only way to build a security strategy that actually works.
Set Up a Proactive Maintenance Routine
Security hardware is just like any other piece of machinery on your site—it needs regular care to perform reliably. Simply waiting for a camera to go dark or a door sensor to fail is just asking for trouble. A proactive maintenance schedule isn't a "nice-to-have"; it's an absolute must.
Your routine should be simple but consistent. Make sure it includes:
Physical Walk-Throughs: Get out there and lay eyes on the equipment. Look for damaged cameras, views blocked by new pallets or overgrown trees, and any signs of tampering with door readers or alarm sensors.
System Health Checks: Log into your security platform regularly. Check for devices that have dropped offline, look for hard drive storage errors, and run diagnostics to catch small issues before they become big problems.
Software and Firmware Updates: This one is huge. Outdated firmware is a gaping security hole. It’s often riddled with known vulnerabilities that hackers are actively looking to exploit, making updates a critical part of your cybersecurity defense.
The single biggest mistake I see facilities make is adopting a "set it and forget it" mindset. Security is a living, breathing process. It demands constant attention, regular testing, and continuous tweaks to stay ahead of new and evolving threats.
Train Your People and Plan Your Response
At the end of the day, your people are your first line of defense. But if they aren’t trained, they can quickly become your weakest link. Everyone who interacts with the system—from your dedicated security guards to floor supervisors—needs to know how it works and what their responsibilities are. They need to understand proper access card etiquette and, just as importantly, who to call the second they see something that doesn’t look right.
Finally, you need a crystal-clear incident response plan. When an alarm goes off at 2 AM on a Saturday, there can be no confusion. Your plan should detail the exact step-by-step procedures for everything: verifying the threat, escalating the response, and coordinating with police or fire departments. Run drills. Practice it. When the pressure is on, you want your team to be able to execute that plan without hesitation.
Common Questions About Industrial Security
When you're tasked with protecting an industrial facility, a lot of questions come up. It's a complex job with high stakes. Let's walk through some of the most common things facility managers and owners ask, breaking them down into practical, straightforward answers.
How Can I Secure My Facility on a Tight Budget?
This is a big one. The key is to be strategic, not just cheap. Start by figuring out where you're most vulnerable with a detailed risk assessment. You can't protect everything at once, so don't try.
Instead, focus your initial investment on the basics that give you the most bang for your buck. Think of it as building a strong foundation. This could mean improving perimeter lighting, reinforcing fences, or installing solid access control systems on your most critical doors and high-value areas.
From there, you can roll out your security plan in phases. Secure the highest-risk zones first, and then expand coverage as more budget becomes available. A hybrid deployment model can also be a game-changer here—using the cloud for management and storage slashes your upfront hardware costs and turns a massive capital expense into a more manageable, predictable operating cost.
What’s the Biggest Mistake Companies Make?
Hands down, the most common and costly mistake is treating security as a one-and-done project. It's that "set it and forget it" mentality. Dropping a ton of money on a fancy system is just the beginning; real security is an ongoing commitment.
The greatest vulnerability in any security system is neglect. A system that isn't regularly maintained, updated, and tested is a security risk in itself, creating a dangerous and false sense of protection.
When you skip regular maintenance, ignore software and firmware updates (a huge cybersecurity risk), or fail to train your team properly, you're essentially letting your investment rust. The best technology in the world is useless if it's not actively managed. Security is a process, not a purchase.
How Are Industrial and Commercial Security Needs Different?
They might seem similar on the surface, but they're worlds apart in practice. The core challenges and what's at stake are completely different.
Industrial sites are tough on equipment. Think extreme temperatures, vibrations, corrosive dust, and sometimes even the risk of explosions. This environment demands specialized, rugged gear that's built to survive, not the standard stuff you'd find in an office building.
The consequences of a security failure are also drastically different.
Commercial Breach: Usually leads to theft or property damage.
Industrial Breach: Could trigger catastrophic operational shutdowns, put workers in serious danger, or lead to environmental disasters.
On top of all that, industrial facilities have the unique and critical challenge of protecting their Operational Technology (OT) networks from cyber threats—a concern that's central to their security strategy.
Ready to build a security strategy that protects your people, assets, and operations? The experts at PCI Audio-Video Security Solutions can design and install a system tailored to your facility's unique challenges. Learn more and schedule your consultation today.







Comments